Role-Based Access Control (RBAC) is nearing the end of its relevance. The static frameworks and manual processes that once formed the backbone of access management are no match for today’s dynamic, complex IT environments. As organizations scale, traditional RBAC systems, constrained by predefined roles and rigid hierarchies, struggle to adapt. They are not just inefficient […]
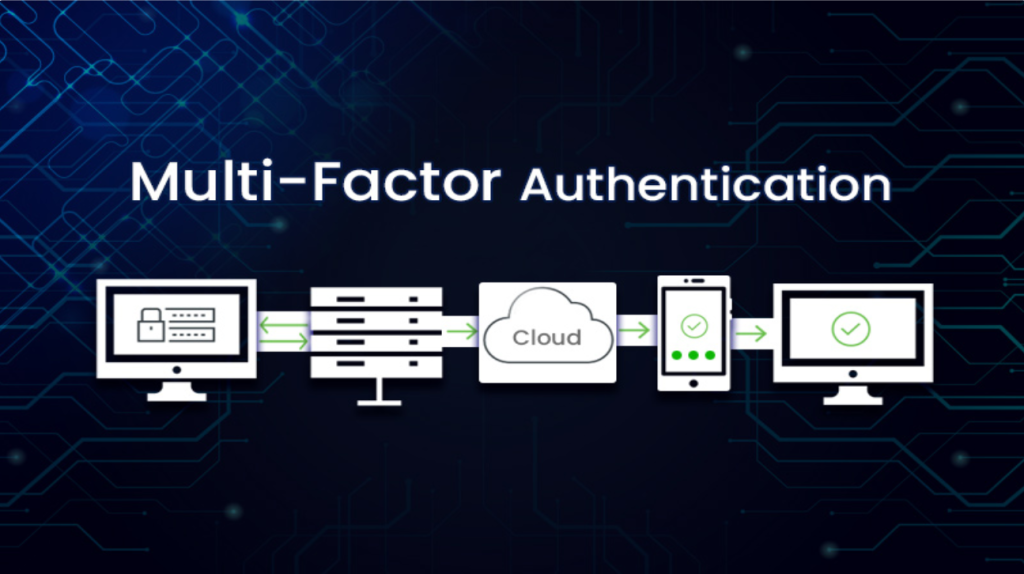
In today’s digital-first world, deploying IAM Managed Services is essential for enterprises to secure sensitive business information, whether related to finances, employee identities, or critical infrastructure. With rising cybersecurity risks, organizations rely on IAM Managed Services to streamline user access, mitigate threats, and ensure compliance with stringent regulations. For business owners, seamless and secure client […]