Swift functioning of IAM systems is imperative for workflow operations, regulatory compliance and security requirements. Information security professionals grapple with the challenge of keeping IT system running, and ensuring that IAM capabilities are aligned to serve the business needs. One also has to ensure just right dependence on centralization and de-centralization for extending permissions, certifications […]
Before we move ahead let me break the biggest myth of present times – Serverless Applications is servers on cloud and are to be managed by the cloud server providers. The term “Serverless” Applications gives an idea that administration of servers, which is one of the biggest headaches for IT teams, is not required. At […]
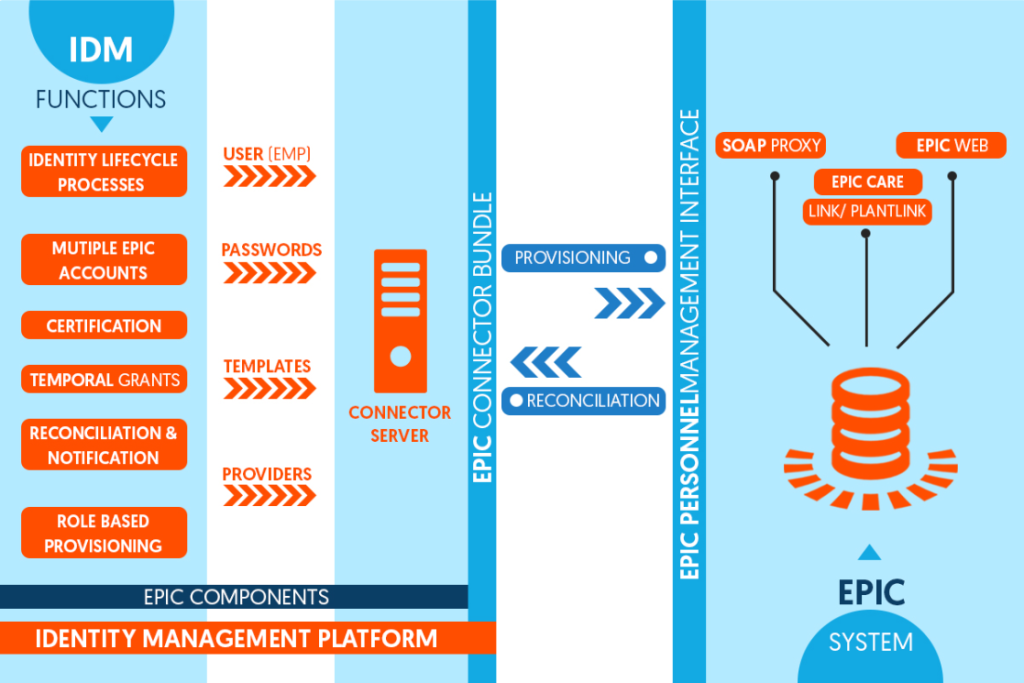
Impactful healthcare/hospital workflows depend on swift functioning of Electronic Medical Records (EMR) Systems such as EPIC, Cerner, Kronos, and other systems. These applications are created to bring ease in management of health records. However, many healthcare clients have shared challenges in managing identities and streamline accesses on EMR Systems. The source of this problem is […]
Are you facing challenges while managing identities on EPIC Systems in your organization? Typically, when an establishment relies too much on an application – strategic foresight in terms of aligning the application with business requirements needs to be just on the spot. Many healthcare establishments rely on EPIC Systems for the management of patient data, […]
I had an amazing discussion on my thoughts shared on Hybrid IT with few of you. One important challenge that was identified was unifying identities in a Hybrid setup. No doubt, identities drive IT processes in an enterprise setup, unification of identities thus becomes an important aspect of IT processes. Many a time, unifying identities […]
Technology is a disruptive game, we discover something new with each passing minute. Businesses are out in the race, they are ready to embrace technology to be closer to business goals, automation and achieve competitive advantage. However, this cannot ignore the security climate associated with new technologies. It is, therefore, important to study and visualize […]
I will pick up from the point where I left – Is Hybrid a problem or an opportunity?The takeaway for me – Hybrid IT will continue to be there for at-least next few years until we have standards, best practices and lessons learnt. For sure, managing Hybrid Eco-System is a challenge! I am assuming that most […]
And how to fix that… Lack of control over SSH Keys is making hackers surpass Secure Shell security layer. The SSH Trick is when hackers use SSH Keys to log into servers. Most organizations are inadequately prepared for detecting a misuse of SSH keys. The trick is predominant, I realized this when I came across […]
Information security starts by controlling – ‘Who’ has ‘What’ access to systems & data and ‘How’ that information is being accessed. Keeping in perspective the security aspect of information routed via SSH Key management, there are a few important questions for IT department heads to ponder over: Enterprises have been using SSH to access IT Systems. However, […]
With the introduction of innovation in technology, a range of security layers rightly get integrated in IT Systems. As conventional security systems cannot address today’s dangerous threat landscape alone – introduction of network forensics and big data analytics is made to capture, process and analyze any security loophole. Furthermore, experts believe that Identity and Access […]
The Internet of Things (IoT) has started to impact the way we function and in the way businesses are conducted. Top industry bodies have made progressive claims on the scope and proliferation of IoT enabled capabilities. A few highlights of IoT proliferation and market share estimates include: As per the highlight, it is correct to […]
Any unknown application, device or IT specific service brought into the IT Systems that is not known to the IT departments can pose a security risk. The risk proposition is based on the premise that these application/device/service are not screened through the on-boarding process, thereby making an entry in the enterprise IT System without required […]
Owing to lack of strategic foresight or sheer laziness, security has traditionally taken a back seat in IT Systems integrations. Lack of security foresight in IT endeavors can impact businesses in the course of time, thus it is recommended to look into security related aspects from the very start — be it at the time […]
Organizations are increasingly incorporating changes in the Software Development Life Cycle (SDLC) in order to improve security posture and create a robust IT System. These changes are aimed to bring security at software development stage itself, rather than incurring expensive fixes for IT vulnerabilities post-implementation of the software. Traditionally, SDLC was focused towards fulfilling specific […]
If we look at the IT departments today, they have become very interesting! It is not just about computing and networks, there is more to it – including IT Security, risk management, access & identity dynamics, cloud, hybrid systems, threat intelligence and the list goes on as we proceed through this article. The leaders and […]
Application security is becoming a prominent aspect of enterprise security and a crucial component in software development and deployment. Companies are investing in app security testing, especially source code review and penetration testing, to create a robust IT System. While IT departments limit using only source code reviews, it is advisable to perform penetration testing. Here’s […]
Come to think of what went on my mind last week, as I savored a cup of hot chocolate, and looked out at snow laden gardens. It was not just a praise for how beautifully nature takes on, it was my time of throwback and, where are we headed? Technology has taken over the way […]
It has been increasingly observed that companies are moving towards managing their IAM projects in-house, rather than engaging an outside vendor. Although, the step has its own merits, starting with gaining greater control over project delivery and saving cost in the short-run, for a long-term perspective, such a move could lead to multiple issues for […]
Before we point at the magic word, Big Data – let’s talk a bit about the volume of data, financial services sector is also facing the challenge of managing the data in a secure manner. API’s are just one aspect of data transfer, but it is important to be integrated smartly. Thus APIs – application […]
An absolute nightmare for an IT security professional is when protected data is accessed by unauthorized personnel. While passwords, firewalls and other basic protection methods are becoming easily ‘hackable’, organizations are seen shifting towards Multi-Factor Authentication (MFA), which includes voice callbacks, SMS’s and OTPs, to combat the issue. Although, MFA has been able to minimize the […]